User Data in AWS
User data in AWS refers to the information or scripts that you can provide to an Amazon Elastic Compute Cloud (EC2) instance during its launch. User data allows you to customize the configuration or behavior of your EC2 instances.
When launching an EC2 instance, we can include a user data script or commands that will be executed automatically once the instance starts running. This user data can be used to perform various tasks such as installing software, configuring settings, running scripts, and more.
Task1:
- Launch EC2 instance with already installed Jenkins on it. Once server shows up in console, hit the IP address in browser and you Jenkins page should be visible.

#!/bin/bash
#installing jenkins on ubuntu
sudo apt-get update -y
sudo apt install openjdk-11-jre -y
curl -fsSL https://pkg.jenkins.io/debian/jenkins.io-2023.key | sudo tee \
/usr/share/keyrings/jenkins-keyring.asc > /dev/null
echo deb [signed-by=/usr/share/keyrings/jenkins-keyring.asc] \
https://pkg.jenkins.io/debian binary/ | sudo tee \
/etc/apt/sources.list.d/jenkins.list > /dev/null
sudo apt-get update -y
sudo apt-get install jenkins -y
sudo systemctl start jenkins
sudo systemctl enable jenkins
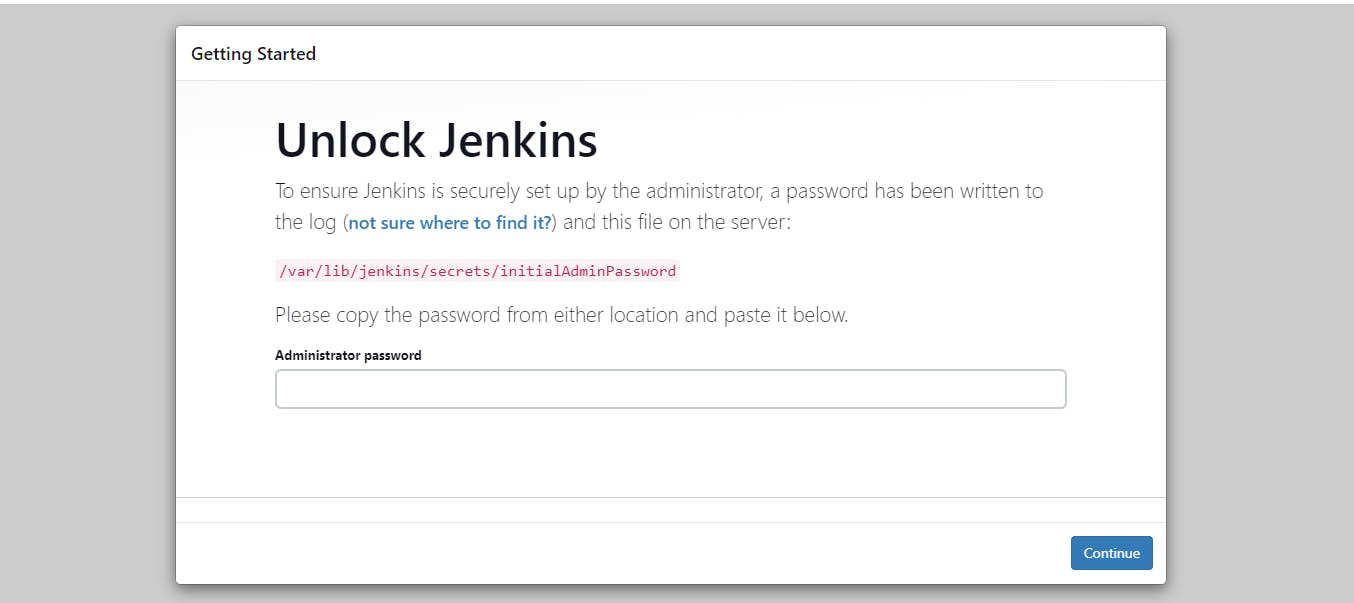
Task2:
Read more on IAM Roles and explain the IAM Users, Groups and Roles in your own terms.
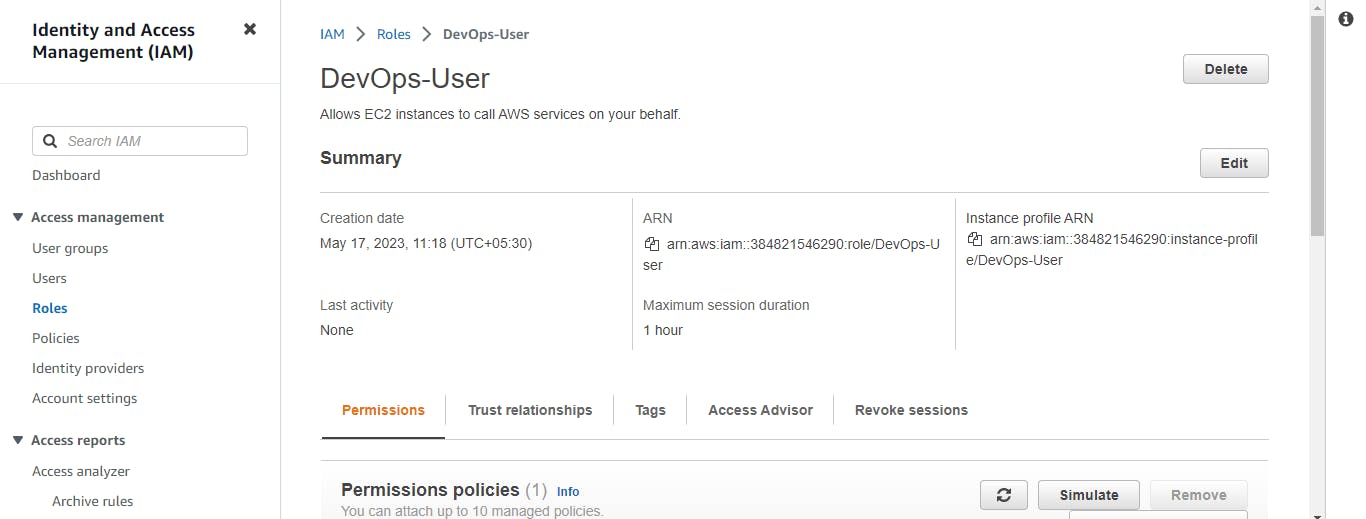
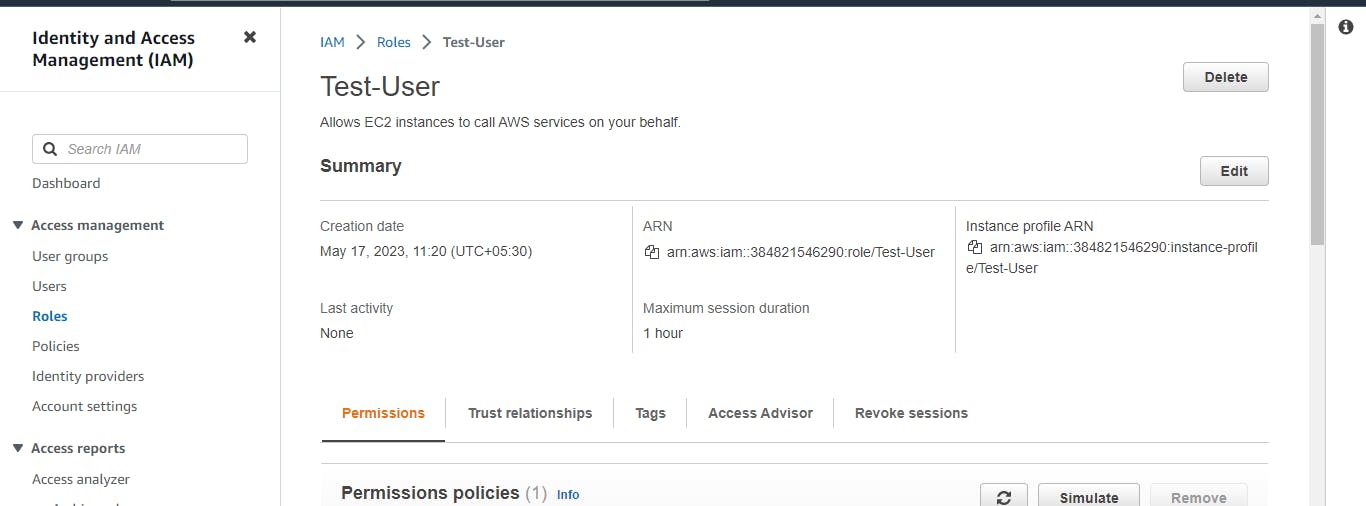
Create three Roles named: DevOps-User, Test-User and Admin.
IAM Users: IAM users are individual identities that you create within AWS Identity and Access Management (IAM). They represent the people or entities that interact with your AWS resources. Each IAM user has unique credentials (username and password or access keys) and can be granted permissions to access specific AWS services and resources.
Think of IAM users as the individuals or entities who have separate accounts or logins to access your AWS environment. For example, you can create an IAM user for yourself, your team members, or any external users who need access to your AWS resources.
IAM Groups: IAM groups are collections or groups of IAM users. They provide a convenient way to manage permissions for multiple users who require the same level of access. Instead of granting permissions to individual users, you can assign permissions to a group, and all users in that group inherit those permissions.
Groups make it easier to manage permissions across multiple users. For example, if you have a team of developers who all need access to the same set of resources, you can create a "Developers" group, assign the necessary permissions to that group, and add all the developers as members. This way, you can easily manage and update permissions for the entire group.
IAM Roles: IAM roles are similar to IAM users but are not tied to a specific individual. Instead, roles are created for specific use cases or services within AWS. Roles define a set of permissions and can be assumed by IAM users, AWS services, or even external identities like federated users.
Roles are useful for granting temporary access or delegating permissions. For example, you can create a role that allows an EC2 instance to access an S3 bucket without having to embed long-term credentials. Another use case is when using AWS services like AWS Lambda, where you can assign an execution role to specify the permissions the Lambda function should have.
Roles provide a flexible way to grant access and ensure security by following the principle of least privilege. They are not tied to specific individuals and can be assumed by different entities as needed.
Create three Roles named: DevOps-User, Test-User and Admin.

I hope you found this blog helpful. Feel free to leave your comments and share your thoughts below and, if you enjoyed this blog, consider sharing it with your network to help others discover the information shared here
