In Kubernetes, ConfigMaps and Secrets are used to store and manage configuration data that is needed by your applications.
ConfigMaps are used to store non-sensitive configuration data such as environment variables, command-line arguments, and configuration files. They can be created and updated independently of the containers that use them. ConfigMaps are usually mounted as volumes inside a container, which allows the application to read the configuration data as if it were a file.
On the other hand, Secrets are used to store sensitive information such as passwords, API keys, and certificates. Secrets are similar to ConfigMaps in that they are also created and managed independently of the containers that use them. However, Secrets are stored in an encrypted format and are only accessible to containers that have the necessary permissions. Secrets can also be mounted as volumes inside a container.
Both ConfigMaps and Secrets can be created using YAML files, and they can be updated using the Kubernetes API or the kubectl command-line tool. By using ConfigMaps and Secrets, you can separate your application code from its configuration data, which makes it easier to manage and update your applications.
Task 1:
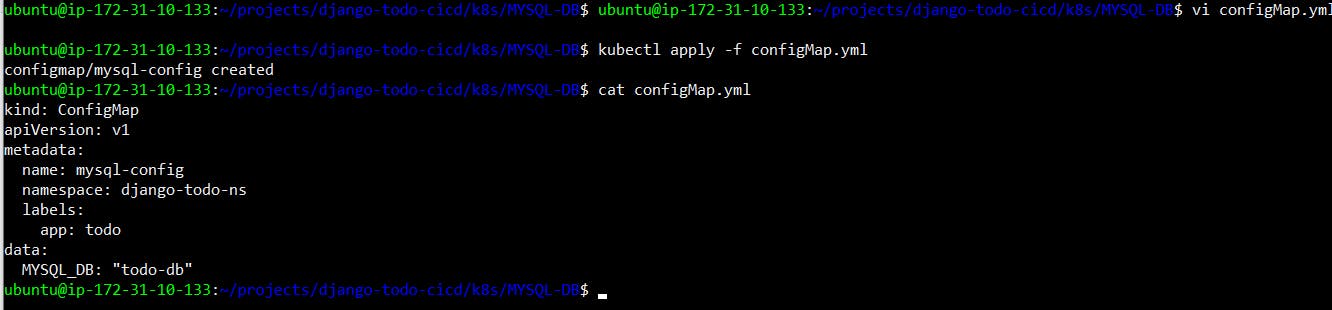
Create a ConfigMap for your Deployment
Create a ConfigMap for your Deployment using a file or the command line
Update the deployment.yml file to include the ConfigMap
Apply the updated deployment using the command:
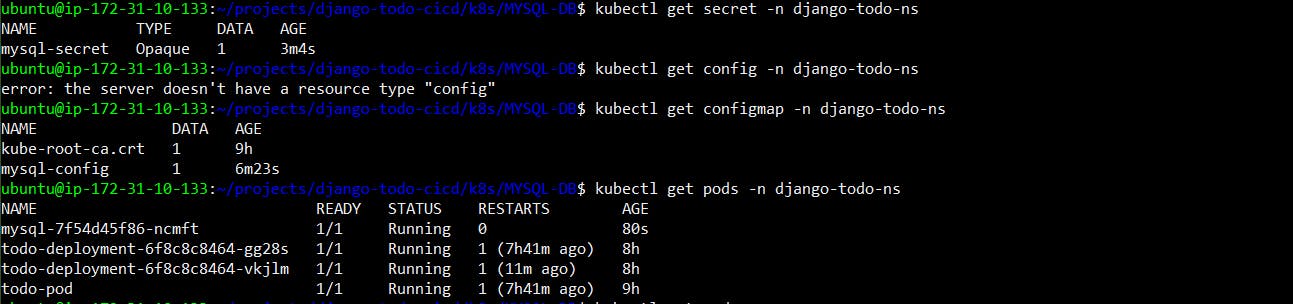
kubectl apply -f deployment.yml -n <namespace-name>Verify that the ConfigMap has been created by checking the status of the ConfigMaps in your Namespace.
Task 2:
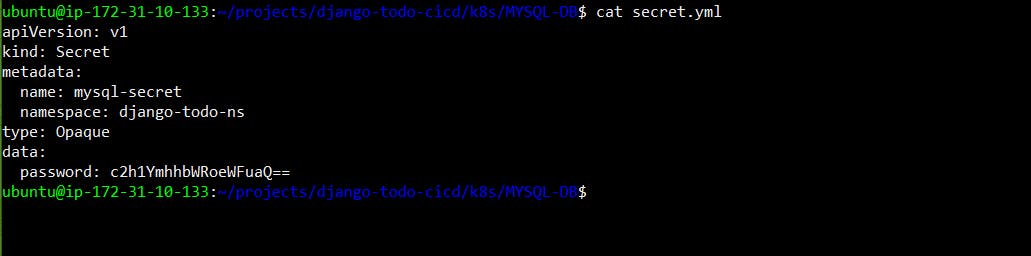
Create a Secret for your Deployment
Create a Secret for your Deployment using a file or the command line
Update the deployment.yml file to include the Secret
Apply the updated deployment using the command:
kubectl apply -f deployment.yml -n <namespace-name>Verify that the Secret has been created by checking the status of the Secrets in your Namespace.
THAT'S ALL FOR TODAY'S LEARNING I HOPE YOU LEARN SOMETHING FROM THIS BLOG
